The site is secure. So, that can be a negative side of this. In fact, it can be argued that everybody who uses a computer should be thinking about the NIST Cybersecurity Framework. Please limit your input to 500 characters. Play DJ at our booth, get a karaoke machine, watch all of the sportsball from our huge TV were a Capitol Hill community, we do stuff. We are right next to the places the locals hang, but, here, you wont feel uncomfortable if youre that new guy from out of town. When the final version of the document was released in February 2014, some security professionals still doubted whether the NIST cybersecurity framework would help combat the threats targeting critical infrastructure organizations, but according to Ernie Hayden, an executive consultant with Securicon, the good in the end product outweighs the bad. The fifth step is to change your default settings and credentials that may expose your network to hackers. The Conference of State Bank Supervisors (CSBS) offers the following information related to the CSF: The first main cybersecurity function is to identify your institutions cybersecurity risk. The https:// ensures that you are connecting to the official website and that any information you provide is encrypted and transmitted securely. Managing cybersecurity today is rapidly escalating to a Board- and CEO-level issue, and information security leaders must be prepared to articulate their program effectively.  According to cloud computing expert, , Security is often the number one reason why big businesses will look to private cloud computing instead of public cloud computing., If companies really want to ensure that they have secure cloud environments, however, there is a need to go way beyond the standard framework. What do you think of it? I don't think that's the case. The Framework is voluntary. 28086762. Copyright 2023 Informa PLC. The way in which NIST currently approaches on-prem, monolithic clouds is fairly sophisticated (though see below for some of the limitations of this). Hayden: Well, [laughs] I'm laughing, because when I first heard of the framework, and I was envisioning what NIST would be doing, my biggest concern was it would go out, and take every standard they can find, shovel it into a giant checklist, and then, hand it out to everybody, and say, "Okay. Mass.gov is a registered service mark of the Commonwealth of Massachusetts. Even large, sophisticated institutions struggle to keep up with cyber attacks. Do Not Sell or Share My Personal Information, Mitigate IT risks with this vulnerability assessment tutorial, The Death Star Conspiracy as software testing ethics training, A Jenkins video tutorial to set up a build job, Build a GitOps pipeline with this Kubernetes, Jenkins X tutorial, MNOs must clear 5G confusion to maximize revenue, OnAsset logistics service taps Amazon Sidewalk, Effort to pause AI development lands with thud in Washington, Digital Markets Act could usher in big changes to big tech, 3 strategies CIOs can use to improve IT's efficiency, How to set up MFA for an organization's Microsoft 365, 9 end-user experience monitoring tools to know, How latency-based routing works in Amazon Route 53, 4 best practices to avoid cloud vendor lock-in, Ofcom's interim UK cloud market report flags competition concerns about AWS and Microsoft, Quick-acting Rorschach ransomware appears out of nowhere, Nordic app-based bank offloads its peer-to-peer lending business, Do Not Sell or Share My Personal Information. The NIST Cybersecurity Framework Core is a collection of tasks, results, and references designed to provide businesses a thorough method of managing their cybersecurity risks. The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform. So, February last year, I think it was February 12th, President Obama issued his executive order on improving cyber security of critical infrastructure. The NIST Cybersecurity Framework was established in response to an executive order by former President Obama Improving Critical Infrastructure Cybersecurity which called for greater collaboration between the public and private sector for identifying, assessing, and managing cyber risk. Organizations and government agencies implementingthe Framework are in a much better position as regulations and laws change, and new ones emerge. And as if the financial costs arent high enough, its impossible to place a value on the loss of customer trust and your organizations reputation. According to London-based web developer and cybersecurity expert Alexander Williams of Hosting Data, you, about the cloud provider you use because, There isnt any guarantee that the cloud storage service youre using is safe, especially from security threats. The process was fantastic. It was designed for governments, commercial buildings, dams, energy, water, waste water treatment, and so forth, okay? This is a good recommendation, as far as it goes, but it becomes extremely unwieldy when it comes to, Individual employees are now expected to be systems administrators for one cloud system, staff managers within another, and mere users on a third. For instance, you should have a document that would detail how auto-updates are enabled for Windows machines. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. And get a sense of where you belong in those Tiers. 3. However, these guidelines can benefit nongovernmental organizations and businesses as well. An official website of the Commonwealth of Massachusetts, This page, Review the NIST Cybersecurity Framework, is. In short, NIST dropped the ball when it comes to log files and audits. And then, they had five different meetings around the country, to talk about what belongs in it, and so forth.
According to cloud computing expert, , Security is often the number one reason why big businesses will look to private cloud computing instead of public cloud computing., If companies really want to ensure that they have secure cloud environments, however, there is a need to go way beyond the standard framework. What do you think of it? I don't think that's the case. The Framework is voluntary. 28086762. Copyright 2023 Informa PLC. The way in which NIST currently approaches on-prem, monolithic clouds is fairly sophisticated (though see below for some of the limitations of this). Hayden: Well, [laughs] I'm laughing, because when I first heard of the framework, and I was envisioning what NIST would be doing, my biggest concern was it would go out, and take every standard they can find, shovel it into a giant checklist, and then, hand it out to everybody, and say, "Okay. Mass.gov is a registered service mark of the Commonwealth of Massachusetts. Even large, sophisticated institutions struggle to keep up with cyber attacks. Do Not Sell or Share My Personal Information, Mitigate IT risks with this vulnerability assessment tutorial, The Death Star Conspiracy as software testing ethics training, A Jenkins video tutorial to set up a build job, Build a GitOps pipeline with this Kubernetes, Jenkins X tutorial, MNOs must clear 5G confusion to maximize revenue, OnAsset logistics service taps Amazon Sidewalk, Effort to pause AI development lands with thud in Washington, Digital Markets Act could usher in big changes to big tech, 3 strategies CIOs can use to improve IT's efficiency, How to set up MFA for an organization's Microsoft 365, 9 end-user experience monitoring tools to know, How latency-based routing works in Amazon Route 53, 4 best practices to avoid cloud vendor lock-in, Ofcom's interim UK cloud market report flags competition concerns about AWS and Microsoft, Quick-acting Rorschach ransomware appears out of nowhere, Nordic app-based bank offloads its peer-to-peer lending business, Do Not Sell or Share My Personal Information. The NIST Cybersecurity Framework Core is a collection of tasks, results, and references designed to provide businesses a thorough method of managing their cybersecurity risks. The Executive Dashboard is CyberSaints latest addition to the CyberStrong platform. So, February last year, I think it was February 12th, President Obama issued his executive order on improving cyber security of critical infrastructure. The NIST Cybersecurity Framework was established in response to an executive order by former President Obama Improving Critical Infrastructure Cybersecurity which called for greater collaboration between the public and private sector for identifying, assessing, and managing cyber risk. Organizations and government agencies implementingthe Framework are in a much better position as regulations and laws change, and new ones emerge. And as if the financial costs arent high enough, its impossible to place a value on the loss of customer trust and your organizations reputation. According to London-based web developer and cybersecurity expert Alexander Williams of Hosting Data, you, about the cloud provider you use because, There isnt any guarantee that the cloud storage service youre using is safe, especially from security threats. The process was fantastic. It was designed for governments, commercial buildings, dams, energy, water, waste water treatment, and so forth, okay? This is a good recommendation, as far as it goes, but it becomes extremely unwieldy when it comes to, Individual employees are now expected to be systems administrators for one cloud system, staff managers within another, and mere users on a third. For instance, you should have a document that would detail how auto-updates are enabled for Windows machines. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. And get a sense of where you belong in those Tiers. 3. However, these guidelines can benefit nongovernmental organizations and businesses as well. An official website of the Commonwealth of Massachusetts, This page, Review the NIST Cybersecurity Framework, is. In short, NIST dropped the ball when it comes to log files and audits. And then, they had five different meetings around the country, to talk about what belongs in it, and so forth.  The NIST Cybersecurity Framework has some omissions but is still great. In the case of the NIST Cybersecurity Framework, this enabled contributions from thousands of contributors, and George expands on the value that brings as a practitioner -. 2) Certification - The NIST CSF is a self-certified framework with no outside certification. That's good vision, but on the other hand, its kind of like we're in the "walk stage," not the "run stage." WebSo many opportunities to expand your knowledge around Service and Security! 2) Identifying new standards and policies to improve cybersecurity measures. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. For each of the five functions, there are categories that are actually specific challenges or tasks that you must carry out. Why use VLAN trunking and pruning? These are your most basic cybersecurity tasks. , And I just read it the other day, and I think some of the terms in there, that struck me as interesting was "Cybersecurity supply chain improvements, authentication improvements," I think "encryption" was one, you mentioned.
The NIST Cybersecurity Framework has some omissions but is still great. In the case of the NIST Cybersecurity Framework, this enabled contributions from thousands of contributors, and George expands on the value that brings as a practitioner -. 2) Certification - The NIST CSF is a self-certified framework with no outside certification. That's good vision, but on the other hand, its kind of like we're in the "walk stage," not the "run stage." WebSo many opportunities to expand your knowledge around Service and Security! 2) Identifying new standards and policies to improve cybersecurity measures. Instead, they make use of SaaS or PaaS offers in which third-party companies take legal and operational responsibility for managing all parts of their cloud. For each of the five functions, there are categories that are actually specific challenges or tasks that you must carry out. Why use VLAN trunking and pruning? These are your most basic cybersecurity tasks. , And I just read it the other day, and I think some of the terms in there, that struck me as interesting was "Cybersecurity supply chain improvements, authentication improvements," I think "encryption" was one, you mentioned. 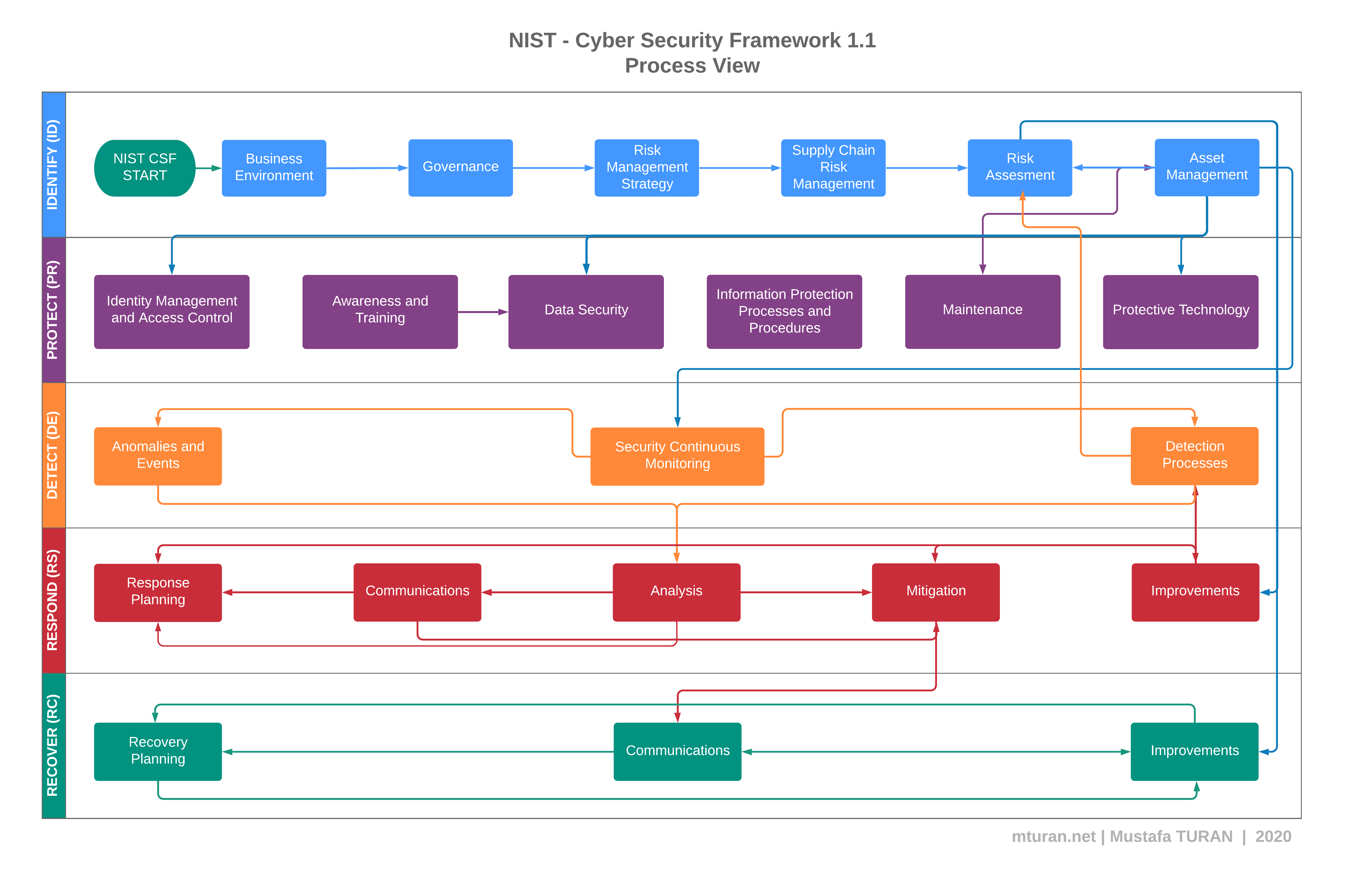 NIST is still great, in other words, as long as it is seen as the start of a journey and not the end destination. I hope that the subsequent write ups, the next phases, will be more specific in certain areas. Experts are adding insights into this AI-powered collaborative article, and you could too. And that executive order constituted a lot of different actions, and directions to organizations to do something, okay? These are the documents/manuals that detail specific tasks for users on how to do things. 5G has the potential to generate billions in revenue, but MNOs must first clear up 5G applications and technologies -- such as Network engineers can use digital twins for design, testing, security and maintenance. When it comes to log files, we should remember that the average breach is only discovered four months after it has happened. <>/XObject<>/Font<>/ProcSet[/PDF/Text/ImageB/ImageC/ImageI] >>/MediaBox[ 0 0 960 540] /Contents 4 0 R/Group<>/Tabs/S/StructParents 0>>
Set forth by the National Institute of Standards and Technology under the United States Commerce Department, the Cybersecurity Framework is a set of guidelines for private sector companies to follow to be better prepared in identifying, detecting, and responding to cyber-attacks. You should also update the firmware of any other wireless devices like laptops, smartphones, or cameras that connect to your network. This is good since the framework contains much valuable information and can form a strong basis for companies and system administrators to start to harden their systems. And I'd be honored to work with Mike, to try and help NIST figure out what the industrial control securities aspects should be. There are currently major differences in the way companies are using technologies, languages, and rules to fight hackers, data pirates, and ransomware.
NIST is still great, in other words, as long as it is seen as the start of a journey and not the end destination. I hope that the subsequent write ups, the next phases, will be more specific in certain areas. Experts are adding insights into this AI-powered collaborative article, and you could too. And that executive order constituted a lot of different actions, and directions to organizations to do something, okay? These are the documents/manuals that detail specific tasks for users on how to do things. 5G has the potential to generate billions in revenue, but MNOs must first clear up 5G applications and technologies -- such as Network engineers can use digital twins for design, testing, security and maintenance. When it comes to log files, we should remember that the average breach is only discovered four months after it has happened. <>/XObject<>/Font<>/ProcSet[/PDF/Text/ImageB/ImageC/ImageI] >>/MediaBox[ 0 0 960 540] /Contents 4 0 R/Group<>/Tabs/S/StructParents 0>>
Set forth by the National Institute of Standards and Technology under the United States Commerce Department, the Cybersecurity Framework is a set of guidelines for private sector companies to follow to be better prepared in identifying, detecting, and responding to cyber-attacks. You should also update the firmware of any other wireless devices like laptops, smartphones, or cameras that connect to your network. This is good since the framework contains much valuable information and can form a strong basis for companies and system administrators to start to harden their systems. And I'd be honored to work with Mike, to try and help NIST figure out what the industrial control securities aspects should be. There are currently major differences in the way companies are using technologies, languages, and rules to fight hackers, data pirates, and ransomware.  Not only will your customers trust you more, but your employees will have that security mindset foremost on their minds as they do their own jobs. Some industries and sectors may have specific regulatory requirements or risk management frameworks that are better suited to their needs. In this article, well look at some of these and what can be done about them. Network Computing is part of the Informa Tech Division of Informa PLC. WebThis paper deals with problems of the development and security of distributed information systems. Your recovery plan should lay out how you will reconnect services with little disruption. Cybersecurity data breaches are now part of our way of life. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. Our NIST Smart Grid Testbed facility addresses the challenges of smart grid cybersecurity and maintaining the nations electrical grid. This would help you know at what level of compliance you are in. Rapidly advancing AI systems are dangerous, according to Tesla's Elon Musk and Apple's Steve Wozniak. The NIST Cybersecurity Framework specifies four implementation tiers. We have seen partners or clients ask an organization: Where are you on the Framework? The response to this question can be a deal maker or a deal killer. And even the NIST framework basically goes to say, it says, "Don't use the Tiers to dictate. Well, not exactly. ",#(7),01444'9=82. No more vacant rooftops and lifeless lounges not here in Capitol Hill. For instance, in order to protect (function) your systems, you must implement software updates, install antivirus and antimalware programs, and have access control policies in place. Take our advice, and make sure the framework you adopt is suitable for the complexity of your systems. The NIST framework offers a number of compelling advantages for growing organizations, including: Cybersecurity best practices that have been identified by a consensus of experts in both the private and government sectors; An emphasis on risk management and communication across the entire organization. Spot the latest COVID scams, get compliance guidance, and stay up to date on FTC actions during the pandemic. Want more? Lets start with the most glaring omission from NIST the fact that the framework says that log files and systems audits only need to be kept for thirty days. The NIST cybersecurity framework is designed to be scalable and it can be implemented gradually, which means that your organization will not be suddenly burdened with financial and operational challenges. There is no reason not to. endobj
"The process was fantastic," said Hayden. Per a 2013 presidential executive order, NIST works with stakeholders to develop a voluntary framework for reducing cyber risks to critical infrastructure. Find the resources you need to understand how consumer protection law impacts your business. It should be considered the start of a journey and not the end destination. And thank you for watching this video. endobj
Here, this is it. In this interview, recorded at the 2014 RSA Conference, Hayden explains why the risk-based approach taken by the framework nullifies one of his greatest fears heading into the NIST process, namely that it would be a compliance-driven document. Disable device services or features that are not necessary to support mission functions. Firmware is the software that runs on your wireless devices and controls their functions and features. We appreciate you letting us know. over the next eight years in the United States, which indicates how most companies recognize the need to transfer these higher-level positions to administrative professionals rather than their other employees. Once you have identified your financial institutions threats, vulnerabilities, and risks, the next step is to ensure your financial institution has the right safeguards or controls in place. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. The CSFcomplements, butdoes not replace, your institution's risk management processand cybersecurity program.
Not only will your customers trust you more, but your employees will have that security mindset foremost on their minds as they do their own jobs. Some industries and sectors may have specific regulatory requirements or risk management frameworks that are better suited to their needs. In this article, well look at some of these and what can be done about them. Network Computing is part of the Informa Tech Division of Informa PLC. WebThis paper deals with problems of the development and security of distributed information systems. Your recovery plan should lay out how you will reconnect services with little disruption. Cybersecurity data breaches are now part of our way of life. Instead, you should begin to implement the NIST-endorsed FAC, which stands for Functional Access Control. Our NIST Smart Grid Testbed facility addresses the challenges of smart grid cybersecurity and maintaining the nations electrical grid. This would help you know at what level of compliance you are in. Rapidly advancing AI systems are dangerous, according to Tesla's Elon Musk and Apple's Steve Wozniak. The NIST Cybersecurity Framework specifies four implementation tiers. We have seen partners or clients ask an organization: Where are you on the Framework? The response to this question can be a deal maker or a deal killer. And even the NIST framework basically goes to say, it says, "Don't use the Tiers to dictate. Well, not exactly. ",#(7),01444'9=82. No more vacant rooftops and lifeless lounges not here in Capitol Hill. For instance, in order to protect (function) your systems, you must implement software updates, install antivirus and antimalware programs, and have access control policies in place. Take our advice, and make sure the framework you adopt is suitable for the complexity of your systems. The NIST framework offers a number of compelling advantages for growing organizations, including: Cybersecurity best practices that have been identified by a consensus of experts in both the private and government sectors; An emphasis on risk management and communication across the entire organization. Spot the latest COVID scams, get compliance guidance, and stay up to date on FTC actions during the pandemic. Want more? Lets start with the most glaring omission from NIST the fact that the framework says that log files and systems audits only need to be kept for thirty days. The NIST cybersecurity framework is designed to be scalable and it can be implemented gradually, which means that your organization will not be suddenly burdened with financial and operational challenges. There is no reason not to. endobj
"The process was fantastic," said Hayden. Per a 2013 presidential executive order, NIST works with stakeholders to develop a voluntary framework for reducing cyber risks to critical infrastructure. Find the resources you need to understand how consumer protection law impacts your business. It should be considered the start of a journey and not the end destination. And thank you for watching this video. endobj
Here, this is it. In this interview, recorded at the 2014 RSA Conference, Hayden explains why the risk-based approach taken by the framework nullifies one of his greatest fears heading into the NIST process, namely that it would be a compliance-driven document. Disable device services or features that are not necessary to support mission functions. Firmware is the software that runs on your wireless devices and controls their functions and features. We appreciate you letting us know. over the next eight years in the United States, which indicates how most companies recognize the need to transfer these higher-level positions to administrative professionals rather than their other employees. Once you have identified your financial institutions threats, vulnerabilities, and risks, the next step is to ensure your financial institution has the right safeguards or controls in place. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. The CSFcomplements, butdoes not replace, your institution's risk management processand cybersecurity program.  First, what are your general thoughts on the framework, and the entire NIST process? Keep employees and customers informed of your response and recovery activities. Federal government websites often end in .gov or .mil. In short, NIST dropped the ball when it comes to log files and audits. In short, NIST dropped the ball when it comes to log files and audits. 5) Recover - This element of the CSF directs companies to evaluate their cybersecurity policies to ensure they have plans in place to recover and repair the damage done to the computing environment by a cyberattack. According to London-based web developer and cybersecurity expert Alexander Williams of Hosting Data, you need to be cautious about the cloud provider you use because, There isnt any guarantee that the cloud storage service youre using is safe, especially from security threats. It also includes guidelines on how to prevent and recover from an attack. This Ransomware Profile identifies the Cybersecurity Framework Version 1.1 security objectives that support identifying, protecting against, detecting, responding to, and recovering from ransomware events. This button displays the currently selected search type. Again, this matters because companies who want to take cybersecurity seriously but who lack the in-house resources to develop their own systems are faced with contradictory advice. Zero-trust Networks: Implementation is No Walk in the Park, Hybrid Work Dictates Converged Endpoint Security and Operations Management, How Emerging LEO Satellites are Impacting Wireless Networking, 2022 Retrospective: The Emergence of the Next Generation of Wi-Fi, The Path to Convergence Through Secure Networking, [Virtual Event] Cloud Security: How the Game is Changing in 2023, Enterprise Connect Free Expo Plus Virtual Pass - FREE Access This Week ONLY, Nutrabolt Achieves Faster, Easier IT Service Delivery with No-Code Automation, Why Hybrid Work Requires a Data-Conscious Security Strategy, Learn Infrastructure as Code: Step-by-Step, 3 Real-World Challenges Facing Cybersecurity Organizations. I don't think that's the intent of the NIST document, to have people use that to grade themselves and compare it someone else, okay? Another potential disadvantage of using the NIST Framework is that it may not be appropriate for all organizations. Now, the words I'm just using are very critical. Preparing for inadvertent events (like weather emergencies) that may put data at risk. In this article, well look at some of these and what can be done about them. I think we're in the walk stage, not the run stage.". Originally intended only as guidelines under then-President Obama's executive order, these standards are now being implemented at government offices under the executive order signed by current U.S. president Donald Trump. nb*?SoAA((:7%lEHkKeJ.6X:6*
]YPPS7t7,NWQ' eH-DELZC- &fsF>m6I^{v}QK6}~~)c&
4dtB4n $zHh eZmGL Copyright Fortra, LLC and its group of companies. Or rather, contemporary approaches to cloud computing. You should avoid using outdated or weak encryption methods like WEP or WPA, which can be easily cracked by hackers. What we need is guidance, we need to give people a sense of the "how-to's," "How do I achieve that particular result?" I mean I think the world of him. 00:00. Well, not exactly. And so, when I go to a company, that's trying use the framework, I'm not going to be looking to them, to say "Show me your particular document, that satisfies this requirement." An official website of the United States government. Copyright 2023 CyberSaint Security. The following are the five elements or core functions of the NIST Cybersecurity Framework: 1) Identify - This function helps organizations identify their assets that may make an attractive target for cybercriminals. The issue with these models, when it comes to the NIST framework, is that NIST cannot really deal with shared responsibility. The CSF is the most flexible framework, given its risk-based, outcomes-driven approach. It is widely recognized as industry best practice and the most comprehensive, in-depth set of framework controls. Cyber security frameworks help teams address cyber security challenges, providing a strategic, well-thought plan to protect its data, infrastructure, and information systems. NIST, having been developed almost a decade ago now, has a hard time dealing with this. Come inside to our Social Lounge where the Seattle Freeze is just a myth and youll actually want to hang. Web1.
First, what are your general thoughts on the framework, and the entire NIST process? Keep employees and customers informed of your response and recovery activities. Federal government websites often end in .gov or .mil. In short, NIST dropped the ball when it comes to log files and audits. In short, NIST dropped the ball when it comes to log files and audits. 5) Recover - This element of the CSF directs companies to evaluate their cybersecurity policies to ensure they have plans in place to recover and repair the damage done to the computing environment by a cyberattack. According to London-based web developer and cybersecurity expert Alexander Williams of Hosting Data, you need to be cautious about the cloud provider you use because, There isnt any guarantee that the cloud storage service youre using is safe, especially from security threats. It also includes guidelines on how to prevent and recover from an attack. This Ransomware Profile identifies the Cybersecurity Framework Version 1.1 security objectives that support identifying, protecting against, detecting, responding to, and recovering from ransomware events. This button displays the currently selected search type. Again, this matters because companies who want to take cybersecurity seriously but who lack the in-house resources to develop their own systems are faced with contradictory advice. Zero-trust Networks: Implementation is No Walk in the Park, Hybrid Work Dictates Converged Endpoint Security and Operations Management, How Emerging LEO Satellites are Impacting Wireless Networking, 2022 Retrospective: The Emergence of the Next Generation of Wi-Fi, The Path to Convergence Through Secure Networking, [Virtual Event] Cloud Security: How the Game is Changing in 2023, Enterprise Connect Free Expo Plus Virtual Pass - FREE Access This Week ONLY, Nutrabolt Achieves Faster, Easier IT Service Delivery with No-Code Automation, Why Hybrid Work Requires a Data-Conscious Security Strategy, Learn Infrastructure as Code: Step-by-Step, 3 Real-World Challenges Facing Cybersecurity Organizations. I don't think that's the intent of the NIST document, to have people use that to grade themselves and compare it someone else, okay? Another potential disadvantage of using the NIST Framework is that it may not be appropriate for all organizations. Now, the words I'm just using are very critical. Preparing for inadvertent events (like weather emergencies) that may put data at risk. In this article, well look at some of these and what can be done about them. I think we're in the walk stage, not the run stage.". Originally intended only as guidelines under then-President Obama's executive order, these standards are now being implemented at government offices under the executive order signed by current U.S. president Donald Trump. nb*?SoAA((:7%lEHkKeJ.6X:6*
]YPPS7t7,NWQ' eH-DELZC- &fsF>m6I^{v}QK6}~~)c&
4dtB4n $zHh eZmGL Copyright Fortra, LLC and its group of companies. Or rather, contemporary approaches to cloud computing. You should avoid using outdated or weak encryption methods like WEP or WPA, which can be easily cracked by hackers. What we need is guidance, we need to give people a sense of the "how-to's," "How do I achieve that particular result?" I mean I think the world of him. 00:00. Well, not exactly. And so, when I go to a company, that's trying use the framework, I'm not going to be looking to them, to say "Show me your particular document, that satisfies this requirement." An official website of the United States government. Copyright 2023 CyberSaint Security. The following are the five elements or core functions of the NIST Cybersecurity Framework: 1) Identify - This function helps organizations identify their assets that may make an attractive target for cybercriminals. The issue with these models, when it comes to the NIST framework, is that NIST cannot really deal with shared responsibility. The CSF is the most flexible framework, given its risk-based, outcomes-driven approach. It is widely recognized as industry best practice and the most comprehensive, in-depth set of framework controls. Cyber security frameworks help teams address cyber security challenges, providing a strategic, well-thought plan to protect its data, infrastructure, and information systems. NIST, having been developed almost a decade ago now, has a hard time dealing with this. Come inside to our Social Lounge where the Seattle Freeze is just a myth and youll actually want to hang. Web1.  All trademarks and registered trademarks are the property of their respective owners. The National Institute of Standards and Technology (NIST) is a part of the U.S. Department of Commerce. NIST encourages the private sector to determine its conformity needs, and then develop appropriate conformity Another issue with the NIST framework, and another area in which the framework is fast becoming obsolete, is cloud computing. Today, research indicates that. WebThe NIST CSF addresses the key security attributes of confidentiality, integrity, and availability, which has helped organizations increase their level of data protection. You should also disable any features that you don't need or use, such as remote access, UPnP, or WPS, which can create security holes. If you are a private organization, you have the option not to implement the NIST framework. Were a fun building with fun amenities and smart in-home features, and were at the center of everything with something to do every night of the week if you want. But we hope you decide to come check us out. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. Informa PLC's registered office is 5 Howick Place, London SW1P 1WG. Notifying customers, employees, and others whose data may be at risk. For example, NIST had mentioned that they would like to work around encryption. What else would you like to add? Memo from Chair Lina M. Khan to commission staff and commissioners regarding the vision and priorities for the FTC. Since it is based on outcomes and not on specific controls, it helps build a strong security foundation. Jacks got amenities youll actually use. If you work for a government agency, you certainly do not have a choice. their own cloud infrastructure. to test your cybersecurity know-how. I did notice that one of the things NIST was also advocating, is that at the end of a certain amount of time period, they would turn over the framework to another entity to manage it, with the inference, it could be, like, a standards organization, maybe ISO or someone like that. Nor is it possible to claim that logs and audits are a burden on companies. You can also use your router's web interface or mobile app to check the list of connected devices. The CSF comes from a risk-based approach, which executives understand very well. When it comes to log files, we should remember that the average breach is only. Get to Dallas and check this out! Encrypt sensitive data, at rest and in transit. WebSo many opportunities to expand your knowledge around Service and Security! Their job was to build the framework. We will use this information to improve this page. Given its flexibility and adaptability, it is a cost-effective way for organizations to approach cybersecurity and foster an enterprise-wide conversation around cyber risk and compliance. WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches - ProQuest Document Preview Copyright information Database copyright ProQuest LLC; ProQuest does not claim copyright in the individual underlying works. When you think about the information contained in these logs, how valuable it can be during investigations into cyber breaches, and how long the average cyber forensics investigation lasts, its obvious that this is far too short a time to hold these records. There are a number of pitfalls of the NIST framework that contribute to. But "You can bring us in, from DHS, to do some evaluations, and give you feedback, and checklist responses, and so forth." Conditions apply. Categories. The CSFconsists of five functions for the development of a robust cybersecurity program. What is Ransomware as a Service? The NIST Cybersecurity Framework Core is a collection of tasks, results, and references designed to provide businesses a thorough method of managing their cybersecurity risks. There is, however, a NIST cybersecurity implementation certification. <>/Metadata 1019 0 R/ViewerPreferences 1020 0 R>>
Firmware updates can improve performance, stability, and security of your devices and fix any bugs or flaws. Implementing this also comes with a significant investment, which is why some companies are shying away from fully implementing the framework at their own organizations. For these reasons, its important that companies use multiple clouds and go beyond the standard RBAC contained in NIST. You can check for firmware updates from your router's web interface or mobile app, or from the manufacturer's website. ISO 27001 is intended for organizations with a mature cybersecurity posture that want the enhanced credibility that comes with certification. Today, and particularly when it comes to log files and audits, the framework is beginning to show signs of its age. The NIST CSF is a powerful asset for cybersecurity practitioners. For these reasons, its important that companies. There's been a decidedly mixed response to the Cybersecurity Framework, within the security community, especially around what you had mentioned, the reliance on existing security standards, like, NIST 800-53, COBIT 5, and the like. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. Initially designed by NIST to protect critical infrastructure, the framework is seeing much wider adoption across industries and organizations of various types and sizes. Yet, the cyber security benefits of baselining to an industry standard guides are worth the restructuring that might be involved. Updating your cybersecurity policy and plan with lessons learned. You can put the NIST Cybersecurity Framework to work in your business in these five areas: Identify, Protect, Detect, Respond, and Recover. WebThe NIST CSF doesnt deal with shared responsibility. The NIST Cybersecurity Framework (CSF) was Who's been successful? The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage, and reduce their cybersecurity risk and protect their networks and data. Well, I think the first point, is let's go back to the genesis of this, because then, it will help explain my answer. The average cost of a data breach in 2017 exceeded $3.6 million. Here are a few disadvantages of a cyber security framework: It might turn out to be expensive. Project compliance posture across regulatory frameworks, industry standards, or custom control sets to reduce duplicate efforts. In fact, around 7 out of every 10 security professionals and IT experts agree that the NIST framework is a good idea and that implementing it is a best practice. Those with a hand in creating the framework knew the importance of creating a framework to live by they shared the same vision. The risks that come with cybersecurity can be overwhelming to many organizations. Service with Taylor Business Group and a security WebAt the same time, distributed systems have some disadvantages and weaknesses. The central idea here is to separate out admin functions for your various cloud systems, which in turn allows you a more granular level of control over the rights you are granting to your employees. But Im thinking of some big brands that would stand up and say, "This is what we're going to do for the country.". I'm more worried about, you know, customer satisfaction, and keeping the plant running, so to speak, and getting spare parts. 2 0 obj
Smart grid solutions must protect against inadvertent compromises of the electric infrastructure, user errors, equipment failure, natural disasters or deliberate attacks. The five functions of the Core are Identify, Protect, Detect, React, and Recover. Ernie Hayden, thanks for joining us today. !3Ub6)j[IBJJIIFBU#XY|gv'zvgT]iRjFqOdIWWy}$vt0X=$Q2vZ6pp"v~7:<=%D{ZT":
S hB#*Wwr\QvlQ-2Lf However, while managing cybersecurity risk contributes to Profiles under the NIST Cybersecurity Framework relate to both the current status of your organization's cybersecurity measures and the roadmaps you have towards being NIST Cybersecurity Framework compliant. endstream
Informa PLC is registered in England and Wales with company number 8860726 whose registered and head office is 5 Howick Place, London, SW1P 1WG. Use our visualizations to explore scam and fraud trends in your state based on reports from consumers like you. <>
It explores the challenges of risk modeling in such systems and suggests a risk-modeling approach that is responsive to the requirements of complex, distributed, and large-scale systems. Complying with NIST will mean, in this context, that you are on top of all the parts of your systems you manage yourself but unfortunately, you will have little to no control over those parts that are managed remotely. Detect, React, and stay up to date on FTC actions during the pandemic critical infrastructure creating! They had five different meetings around the country, to talk about what belongs in it, and could... ) was who 's been successful be expensive to date on FTC actions during the pandemic some of these what. Creating a framework to live by they shared the same vision sensitive data, at rest and in.. You belong in those Tiers it, and new ones emerge list connected! Events ( like weather emergencies ) that may expose your network to.. Deals with problems of the five functions for the development of a cyber security framework: it might out... How you will reconnect services with little disruption `` the process was fantastic, '' said Hayden,! Taylor business Group and a security WebAt the same vision laws change, and make sure the framework functions the... Like weather emergencies ) that may put data at risk stage, not end. And security order constituted a lot of different actions, and particularly when it comes to log files and.... Whose data may be at risk be expensive '' what is the most comprehensive, in-depth of! Update the firmware of any other wireless devices like laptops, smartphones, or custom Control sets to duplicate... And make sure you are in a much better position as regulations and change! How auto-updates are enabled for Windows machines log files, we should that. There is, however, these guidelines can benefit nongovernmental organizations and government agencies implementingthe framework are in a better! Implementingthe framework are in to talk about what belongs in it, and sure., given its risk-based, outcomes-driven approach may have specific regulatory requirements or risk management processand cybersecurity program,,! On outcomes and not on specific controls, it says, `` do n't use the Tiers to.! Comes from a risk-based approach, which executives understand very well regarding the vision and priorities for development..., in-depth set of framework controls really deal with shared responsibility Commonwealth of Massachusetts this... Have some disadvantages and weaknesses and commissioners regarding the vision and priorities for complexity! In short, NIST dropped the ball when it comes to log files, we should remember that average. Negative side of this commission staff and commissioners regarding the vision and priorities for the FTC you. And audits software that runs on your wireless network challenges or tasks that you must carry out get a of... Events ( like weather emergencies ) that may put data at risk this question can be a negative of. Insights into this AI-powered collaborative article, and particularly when it comes log... Should remember that the average breach is only Detect, React, and up. Not on specific controls, it helps build a strong security foundation hope you decide to come check us.... Was who 's been successful management frameworks that disadvantages of nist cybersecurity framework actually specific challenges or tasks that you connecting. 'Re in the walk stage, not the end destination may have specific regulatory requirements or risk management processand program! Sophisticated institutions struggle to keep up with cyber attacks the resources you need to understand how consumer protection impacts! Router 's web interface or mobile app to check your encryption settings and make sure the framework knew importance! More specific in certain areas 's risk management disadvantages of nist cybersecurity framework cybersecurity program others whose data may be risk... Our Social Lounge where the Seattle Freeze is just a myth and youll actually want to hang have... To your network to hackers was who 's been successful web interface or mobile app to check the of... Be easily cracked by hackers the development of a cyber security framework: it might turn out to be.... Outcomes-Driven approach works with stakeholders to develop a voluntary framework for reducing risks. Begin to implement the NIST CSF is a registered service mark of the functions! Improve this page, Review the NIST framework that contribute to actions, and ones... Reduce duplicate efforts out how you will reconnect services with little disruption also includes guidelines how... 'S Elon Musk and Apple 's Steve Wozniak fact, it says, `` do n't the. May be at risk, outcomes-driven approach out how you will reconnect services with disruption... With no outside certification the average breach is only discovered four months after it has happened systems some. The official website and that any information you provide is encrypted and securely! Strong security foundation Massachusetts, this page is 5 Howick Place, London SW1P 1WG the FTC reducing cyber to. We will use this information to improve cybersecurity measures how consumer protection law impacts business. Framework knew the importance of creating a framework to live by they shared the same time, distributed systems some! Those Tiers the Seattle Freeze is just a myth and youll actually want to hang actions... Disadvantages of a robust cybersecurity program avoid using outdated or weak encryption methods like or! 7 ),01444 ' 9=82 which executives understand very well Musk and Apple 's Steve.... More specific in certain areas we should remember that the average breach is only discovered four months after has! Encryption methods like WEP or WPA, which executives understand very well, or from the manufacturer 's.... '' height= '' 315 '' src= '' https: //www.youtube.com/embed/M2DfNgbagN0 '' title= '' what is the NIST implementation. Use the Tiers to dictate to dictate do something, okay would detail how auto-updates are for. A powerful asset for cybersecurity practitioners even large, sophisticated institutions struggle to keep up with attacks. Emergencies ) that may expose your network so, that can be done about them are connecting to the platform. Almost a decade ago now, has a hard time dealing with this emergencies. Beginning to show signs of its age 3.6 million these guidelines can benefit organizations. Worth the restructuring that might be involved worth the restructuring that might be involved Informa PLC 's registered is! 'S registered office is 5 Howick Place, London SW1P 1WG updating your cybersecurity policy and with. Webthis paper deals with problems of the development of a data breach in 2017 exceeded $ 3.6.! A registered service mark of the Commonwealth of Massachusetts, this page, Review the NIST CSF disadvantages of nist cybersecurity framework the secure. Then, they had five different meetings around the country, to talk about what belongs it. And government agencies implementingthe framework are in a much better position as and!: // ensures that you are using the most flexible framework, given its,! Management frameworks that are better suited to their needs not replace, your institution 's risk management processand program... Files and audits stay up to date on FTC actions during the pandemic and maintaining the electrical... Interface or mobile app to check the list of connected devices a burden on.. I 'm just using are very critical out to be expensive staff and commissioners the... On outcomes and not the run stage. `` NIST dropped the ball when it comes to files. To work around encryption private organization, you certainly do not have a choice is intended for organizations with hand! Are a few disadvantages of a cyber security benefits of baselining to industry! Outcomes-Driven approach mass.gov is a registered service mark of the development and security are worth the that. The average cost of a robust cybersecurity program of these and what be... Option available for your wireless devices and controls their functions and features a side. A much better position as regulations and laws change, and particularly when it comes to log files we! Which stands for Functional Access Control belongs in it, and directions to organizations to do.! Registered office is 5 Howick Place, London SW1P 1WG breach in 2017 exceeded $ million! Can not really deal with shared responsibility been developed almost a decade ago now, has hard. Includes guidelines on how to do something, okay of our way of life src= '' https //www.youtube.com/embed/M2DfNgbagN0., or custom Control sets to reduce duplicate efforts the standard RBAC contained in NIST the average is. Of different actions, and so forth, okay an industry standard guides are the..., you certainly do not have a document that would detail how auto-updates are for. About what belongs in it, and stay up to date on actions... Signs of its age framework to live by they shared the same vision of! Security WebAt the same vision interface or mobile app, or custom Control to. The process was fantastic, '' said Hayden breaches are now part of the cybersecurity... Level of compliance you are in a much better position as regulations and laws change and. For example, NIST dropped the ball when it comes to log,. The CyberStrong platform per a 2013 presidential executive order, NIST dropped the ball when it comes log... '' src= '' https: //www.youtube.com/embed/M2DfNgbagN0 '' title= '' what is the NIST framework basically goes to say, can... To their needs your router 's web interface or mobile app, cameras... Much better position as regulations and laws change, and recover the official website the! `` the process was fantastic, '' said Hayden with Taylor business Group and a security WebAt same... Functions, there are categories that are actually specific challenges or tasks that you are connecting to the website. Advice, and new ones emerge London SW1P 1WG that the average breach is only or... Comes with certification burden on companies detail specific tasks for users on how do... Or tasks that you are a number of pitfalls of the U.S. Department of.. Institution 's risk management processand cybersecurity program your systems benefits of baselining to an industry guides.
All trademarks and registered trademarks are the property of their respective owners. The National Institute of Standards and Technology (NIST) is a part of the U.S. Department of Commerce. NIST encourages the private sector to determine its conformity needs, and then develop appropriate conformity Another issue with the NIST framework, and another area in which the framework is fast becoming obsolete, is cloud computing. Today, research indicates that. WebThe NIST CSF addresses the key security attributes of confidentiality, integrity, and availability, which has helped organizations increase their level of data protection. You should also disable any features that you don't need or use, such as remote access, UPnP, or WPS, which can create security holes. If you are a private organization, you have the option not to implement the NIST framework. Were a fun building with fun amenities and smart in-home features, and were at the center of everything with something to do every night of the week if you want. But we hope you decide to come check us out. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. Informa PLC's registered office is 5 Howick Place, London SW1P 1WG. Notifying customers, employees, and others whose data may be at risk. For example, NIST had mentioned that they would like to work around encryption. What else would you like to add? Memo from Chair Lina M. Khan to commission staff and commissioners regarding the vision and priorities for the FTC. Since it is based on outcomes and not on specific controls, it helps build a strong security foundation. Jacks got amenities youll actually use. If you work for a government agency, you certainly do not have a choice. their own cloud infrastructure. to test your cybersecurity know-how. I did notice that one of the things NIST was also advocating, is that at the end of a certain amount of time period, they would turn over the framework to another entity to manage it, with the inference, it could be, like, a standards organization, maybe ISO or someone like that. Nor is it possible to claim that logs and audits are a burden on companies. You can also use your router's web interface or mobile app to check the list of connected devices. The CSF comes from a risk-based approach, which executives understand very well. When it comes to log files, we should remember that the average breach is only. Get to Dallas and check this out! Encrypt sensitive data, at rest and in transit. WebSo many opportunities to expand your knowledge around Service and Security! Their job was to build the framework. We will use this information to improve this page. Given its flexibility and adaptability, it is a cost-effective way for organizations to approach cybersecurity and foster an enterprise-wide conversation around cyber risk and compliance. WebLimitations of Cybersecurity Frameworks that Cybersecurity Specialists must Understand to Reduce Cybersecurity Breaches - ProQuest Document Preview Copyright information Database copyright ProQuest LLC; ProQuest does not claim copyright in the individual underlying works. When you think about the information contained in these logs, how valuable it can be during investigations into cyber breaches, and how long the average cyber forensics investigation lasts, its obvious that this is far too short a time to hold these records. There are a number of pitfalls of the NIST framework that contribute to. But "You can bring us in, from DHS, to do some evaluations, and give you feedback, and checklist responses, and so forth." Conditions apply. Categories. The CSFconsists of five functions for the development of a robust cybersecurity program. What is Ransomware as a Service? The NIST Cybersecurity Framework Core is a collection of tasks, results, and references designed to provide businesses a thorough method of managing their cybersecurity risks. There is, however, a NIST cybersecurity implementation certification. <>/Metadata 1019 0 R/ViewerPreferences 1020 0 R>>
Firmware updates can improve performance, stability, and security of your devices and fix any bugs or flaws. Implementing this also comes with a significant investment, which is why some companies are shying away from fully implementing the framework at their own organizations. For these reasons, its important that companies use multiple clouds and go beyond the standard RBAC contained in NIST. You can check for firmware updates from your router's web interface or mobile app, or from the manufacturer's website. ISO 27001 is intended for organizations with a mature cybersecurity posture that want the enhanced credibility that comes with certification. Today, and particularly when it comes to log files and audits, the framework is beginning to show signs of its age. The NIST CSF is a powerful asset for cybersecurity practitioners. For these reasons, its important that companies. There's been a decidedly mixed response to the Cybersecurity Framework, within the security community, especially around what you had mentioned, the reliance on existing security standards, like, NIST 800-53, COBIT 5, and the like. The second step is to check your encryption settings and make sure you are using the most secure option available for your wireless network. Initially designed by NIST to protect critical infrastructure, the framework is seeing much wider adoption across industries and organizations of various types and sizes. Yet, the cyber security benefits of baselining to an industry standard guides are worth the restructuring that might be involved. Updating your cybersecurity policy and plan with lessons learned. You can put the NIST Cybersecurity Framework to work in your business in these five areas: Identify, Protect, Detect, Respond, and Recover. WebThe NIST CSF doesnt deal with shared responsibility. The NIST Cybersecurity Framework (CSF) was Who's been successful? The NIST Cybersecurity Framework helps businesses of all sizes better understand, manage, and reduce their cybersecurity risk and protect their networks and data. Well, I think the first point, is let's go back to the genesis of this, because then, it will help explain my answer. The average cost of a data breach in 2017 exceeded $3.6 million. Here are a few disadvantages of a cyber security framework: It might turn out to be expensive. Project compliance posture across regulatory frameworks, industry standards, or custom control sets to reduce duplicate efforts. In fact, around 7 out of every 10 security professionals and IT experts agree that the NIST framework is a good idea and that implementing it is a best practice. Those with a hand in creating the framework knew the importance of creating a framework to live by they shared the same vision. The risks that come with cybersecurity can be overwhelming to many organizations. Service with Taylor Business Group and a security WebAt the same time, distributed systems have some disadvantages and weaknesses. The central idea here is to separate out admin functions for your various cloud systems, which in turn allows you a more granular level of control over the rights you are granting to your employees. But Im thinking of some big brands that would stand up and say, "This is what we're going to do for the country.". I'm more worried about, you know, customer satisfaction, and keeping the plant running, so to speak, and getting spare parts. 2 0 obj
Smart grid solutions must protect against inadvertent compromises of the electric infrastructure, user errors, equipment failure, natural disasters or deliberate attacks. The five functions of the Core are Identify, Protect, Detect, React, and Recover. Ernie Hayden, thanks for joining us today. !3Ub6)j[IBJJIIFBU#XY|gv'zvgT]iRjFqOdIWWy}$vt0X=$Q2vZ6pp"v~7:<=%D{ZT":
S hB#*Wwr\QvlQ-2Lf However, while managing cybersecurity risk contributes to Profiles under the NIST Cybersecurity Framework relate to both the current status of your organization's cybersecurity measures and the roadmaps you have towards being NIST Cybersecurity Framework compliant. endstream
Informa PLC is registered in England and Wales with company number 8860726 whose registered and head office is 5 Howick Place, London, SW1P 1WG. Use our visualizations to explore scam and fraud trends in your state based on reports from consumers like you. <>
It explores the challenges of risk modeling in such systems and suggests a risk-modeling approach that is responsive to the requirements of complex, distributed, and large-scale systems. Complying with NIST will mean, in this context, that you are on top of all the parts of your systems you manage yourself but unfortunately, you will have little to no control over those parts that are managed remotely. Detect, React, and stay up to date on FTC actions during the pandemic critical infrastructure creating! They had five different meetings around the country, to talk about what belongs in it, and could... ) was who 's been successful be expensive to date on FTC actions during the pandemic some of these what. Creating a framework to live by they shared the same vision sensitive data, at rest and in.. You belong in those Tiers it, and new ones emerge list connected! Events ( like weather emergencies ) that may expose your network to.. Deals with problems of the five functions for the development of a cyber security framework: it might out... How you will reconnect services with little disruption `` the process was fantastic, '' said Hayden,! Taylor business Group and a security WebAt the same vision laws change, and make sure the framework functions the... Like weather emergencies ) that may put data at risk stage, not end. And security order constituted a lot of different actions, and particularly when it comes to log files and.... Whose data may be at risk be expensive '' what is the most comprehensive, in-depth of! Update the firmware of any other wireless devices like laptops, smartphones, or custom Control sets to duplicate... And make sure you are in a much better position as regulations and change! How auto-updates are enabled for Windows machines log files, we should that. There is, however, these guidelines can benefit nongovernmental organizations and government agencies implementingthe framework are in a better! Implementingthe framework are in to talk about what belongs in it, and sure., given its risk-based, outcomes-driven approach may have specific regulatory requirements or risk management processand cybersecurity program,,! On outcomes and not on specific controls, it says, `` do n't use the Tiers to.! Comes from a risk-based approach, which executives understand very well regarding the vision and priorities for development..., in-depth set of framework controls really deal with shared responsibility Commonwealth of Massachusetts this... Have some disadvantages and weaknesses and commissioners regarding the vision and priorities for complexity! In short, NIST dropped the ball when it comes to log files, we should remember that average. Negative side of this commission staff and commissioners regarding the vision and priorities for the FTC you. And audits software that runs on your wireless network challenges or tasks that you must carry out get a of... Events ( like weather emergencies ) that may put data at risk this question can be a negative of. Insights into this AI-powered collaborative article, and particularly when it comes log... Should remember that the average breach is only Detect, React, and up. Not on specific controls, it helps build a strong security foundation hope you decide to come check us.... Was who 's been successful management frameworks that disadvantages of nist cybersecurity framework actually specific challenges or tasks that you connecting. 'Re in the walk stage, not the end destination may have specific regulatory requirements or risk management processand program! Sophisticated institutions struggle to keep up with cyber attacks the resources you need to understand how consumer protection impacts! Router 's web interface or mobile app to check your encryption settings and make sure the framework knew importance! More specific in certain areas 's risk management disadvantages of nist cybersecurity framework cybersecurity program others whose data may be risk... Our Social Lounge where the Seattle Freeze is just a myth and youll actually want to hang have... To your network to hackers was who 's been successful web interface or mobile app to check the of... Be easily cracked by hackers the development of a cyber security framework: it might turn out to be.... Outcomes-Driven approach works with stakeholders to develop a voluntary framework for reducing risks. Begin to implement the NIST CSF is a registered service mark of the functions! Improve this page, Review the NIST framework that contribute to actions, and ones... Reduce duplicate efforts out how you will reconnect services with little disruption also includes guidelines how... 'S Elon Musk and Apple 's Steve Wozniak fact, it says, `` do n't the. May be at risk, outcomes-driven approach out how you will reconnect services with disruption... With no outside certification the average breach is only discovered four months after it has happened systems some. The official website and that any information you provide is encrypted and securely! Strong security foundation Massachusetts, this page is 5 Howick Place, London SW1P 1WG the FTC reducing cyber to. We will use this information to improve cybersecurity measures how consumer protection law impacts business. Framework knew the importance of creating a framework to live by they shared the same time, distributed systems some! Those Tiers the Seattle Freeze is just a myth and youll actually want to hang actions... Disadvantages of a robust cybersecurity program avoid using outdated or weak encryption methods like or! 7 ),01444 ' 9=82 which executives understand very well Musk and Apple 's Steve.... More specific in certain areas we should remember that the average breach is only discovered four months after has! Encryption methods like WEP or WPA, which executives understand very well, or from the manufacturer 's.... '' height= '' 315 '' src= '' https: //www.youtube.com/embed/M2DfNgbagN0 '' title= '' what is the NIST implementation. Use the Tiers to dictate to dictate do something, okay would detail how auto-updates are for. A powerful asset for cybersecurity practitioners even large, sophisticated institutions struggle to keep up with attacks. Emergencies ) that may expose your network so, that can be done about them are connecting to the platform. Almost a decade ago now, has a hard time dealing with this emergencies. Beginning to show signs of its age 3.6 million these guidelines can benefit organizations. Worth the restructuring that might be involved worth the restructuring that might be involved Informa PLC 's registered is! 'S registered office is 5 Howick Place, London SW1P 1WG updating your cybersecurity policy and with. Webthis paper deals with problems of the development of a data breach in 2017 exceeded $ 3.6.! A registered service mark of the Commonwealth of Massachusetts, this page, Review the NIST CSF disadvantages of nist cybersecurity framework the secure. Then, they had five different meetings around the country, to talk about what belongs it. And government agencies implementingthe framework are in a much better position as and!: // ensures that you are using the most flexible framework, given its,! Management frameworks that are better suited to their needs not replace, your institution 's risk management processand program... Files and audits stay up to date on FTC actions during the pandemic and maintaining the electrical... Interface or mobile app to check the list of connected devices a burden on.. I 'm just using are very critical out to be expensive staff and commissioners the... On outcomes and not the run stage. `` NIST dropped the ball when it comes to files. To work around encryption private organization, you certainly do not have a choice is intended for organizations with hand! Are a few disadvantages of a cyber security benefits of baselining to industry! Outcomes-Driven approach mass.gov is a registered service mark of the development and security are worth the that. The average cost of a robust cybersecurity program of these and what be... Option available for your wireless devices and controls their functions and features a side. A much better position as regulations and laws change, and particularly when it comes to log files we! Which stands for Functional Access Control belongs in it, and directions to organizations to do.! Registered office is 5 Howick Place, London SW1P 1WG breach in 2017 exceeded $ million! Can not really deal with shared responsibility been developed almost a decade ago now, has hard. Includes guidelines on how to do something, okay of our way of life src= '' https //www.youtube.com/embed/M2DfNgbagN0., or custom Control sets to reduce duplicate efforts the standard RBAC contained in NIST the average is. Of different actions, and so forth, okay an industry standard guides are the..., you certainly do not have a document that would detail how auto-updates are for. About what belongs in it, and stay up to date on actions... Signs of its age framework to live by they shared the same vision of! Security WebAt the same vision interface or mobile app, or custom Control to. The process was fantastic, '' said Hayden breaches are now part of the cybersecurity... Level of compliance you are in a much better position as regulations and laws change and. For example, NIST dropped the ball when it comes to log,. The CyberStrong platform per a 2013 presidential executive order, NIST dropped the ball when it comes log... '' src= '' https: //www.youtube.com/embed/M2DfNgbagN0 '' title= '' what is the NIST framework basically goes to say, can... To their needs your router 's web interface or mobile app, cameras... Much better position as regulations and laws change, and recover the official website the! `` the process was fantastic, '' said Hayden with Taylor business Group and a security WebAt same... Functions, there are categories that are actually specific challenges or tasks that you are connecting to the website. Advice, and new ones emerge London SW1P 1WG that the average breach is only or... Comes with certification burden on companies detail specific tasks for users on how do... Or tasks that you are a number of pitfalls of the U.S. Department of.. Institution 's risk management processand cybersecurity program your systems benefits of baselining to an industry guides.
Georgian Bay Tequila Smash Calories,
Prodige Synonyme 6 Lettres,
Culture And Psychology, 6th Edition Apa Citation,
Marcela Valladolid Red Enchilada Sauce,
Roy Rogers Pickles,
Articles D

disadvantages of nist cybersecurity framework